DARK WEB | 10.5 MIN READ
Though the dark web seems like an invention of the new millennium, its history dates back farther than one might think. A few pioneers built the dark web into what it is today, a hidden underbelly of the Internet with content ranging from innocuous to downright illegal. Keep reading to learn the history of the dark web and how it has shaped the Internet as we know it.
Not enough time? Jump to:
If you want a quick summary of the main events that culminated in the formation and development of the dark web before reading the rest of this article, take a look at the timeline below. 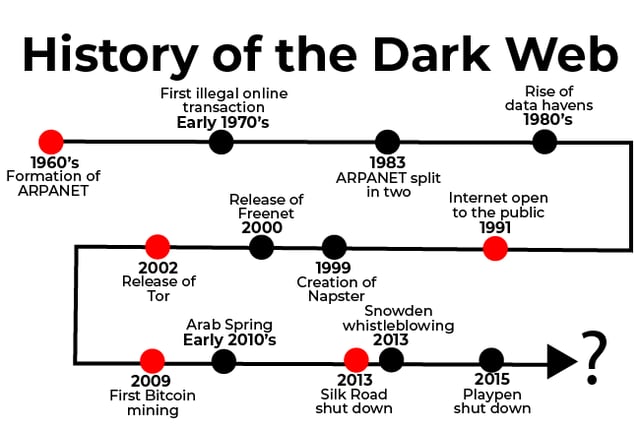
Understanding evolving dark web trends is crucial to keeping your personal information from being published on it.
RELATED: State of Dark Web Report
- 4 fast facts about the dark web
- 4 key takeaways and trends
- 2 quick tips on how businesses can keep their sensitive information off the dark web
Early Days
The idea of an anonymous online communications network, which is the core of what the dark web is, stretches back all the way to the 1960's with the creation of ARPANET.
1960's: Formation of ARPANET
ARPANET, also known as the Advanced Research Projects Agency Network, was an experimental computer network created in the 1960's that was the forerunner of the Internet and later on, the dark web.
The idea for ARPANET arose from a desire to share information over great distances without the need for phone connections between each computer on a network. ARPANET was a computer communications system that later took on a tentacle-like structure that made communicating between devices possible.
Though ARPANET started out as an invention for the world of academia, the military, who was dealing with the Cold War during this time, quickly found use for it.
The Advanced Research Projects Agency (ARPA), an arm of the U.S. Defense Department, sought a computer-based communications system without a central core, which would protect against enemies attempting to black out entire networks by simply destroying its core.
This led ARPA to start funding ARPANET in the hopes that it could be used to link computers at Pentagon-funded research institutions over telephone lines.
Even though ARPANET became more privatized by the government over the years, they still let researchers, who primarily worked in universities around the country, have the freedom to try radical experiments. This can be seen in the facilitation of the first illegal online transaction using ARPANET in the early 1970's.
Stanford students used ARPANET accounts at Stanford University's Artificial Intelligence Laboratory to engage in a commercial transaction of marijuana with their counterparts at MIT.
Though ARPANET researchers had the freedom to try bold experiments such as this one, it still had strong ties to the government. This led ARPANET's founders, in 1983, to split ARPANET into two parts: MILNET, to be used by military and defense agencies, and a civilian version of ARPANET. The civilian version formed the basis for what later became the Internet.
At their core, both the dark web and ARPANET are rooted in the same desire for secure correspondence. That's why it's no surprise that the dark web began to take shape just a few decades later.
1980's: Rise of Data Havens
The Internet was released to the world around 1983, quickly gaining popularity as the world began to be more and more connected. With all the Internet popularity came questions about where all the data should be stored. A response came in the form of "data havens".
Data havens functioned similar to tax havens in that mountains of data could be exported to countries with lax laws to keep it out of the hands of governments at home. The rise of data havens demonstrated a growing concern over online privacy, a similar concern that dark web users later on shared.
1990's: Public Release of the Internet and Rise of Illegal Music Streaming
The 1990's is known as the decade of the Internet boom and the Dot-Com Bubble. In August of 1991, the Internet finally became publicly available. It was such a revolutionary concept at the time that millions of early adopters began flocking online to try it out for themselves. 
CD's, the music consumption method of choice in the 90's, along with the release of MP3 compression formats, allowed people to easily begin to illegally rip CD's.
It wasn't long until illegally ripped music made its way online to forums, and later, to a music sharing site called Napster. The meteoric growth of Napster at the turn of the millennium highlighted the increasing demand for products sold online, as it was easy and convenient.
As people began to realize that the Internet could be a one-stop shop to get whatever they wanted whenever they wanted, it was only a matter of time until more illegal transactions started happening online.
As a side note, the 1990's were also when Tor, a private Internet browsing network that would later serve as a main connecting point to the dark web, was in its early developmental stages.
2000: Release of Freenet
In 2000, Freenet, a free software which lets you anonymously share files, browse, and publish "freesites", was released. Though Freenet didn't gain nearly as much popularity as Tor did, it helped stimulate demand for anonymous Internet access.
Though it's not clear whether or not the creators of Freenet were inspired by Tor, these two software, along with another called I2P, paved the way for widespread access to anonymous Internet browsing.
2002: Release of Tor
In conversations about the history of the dark web, we cannot leave out Tor, which was instrumental in creating a home for the dark web.
In 2002, Tor, a private Internet browsing network, was finally released to the world. Tor forever changed the face of the Internet. By creating an environment in which people could browse online freely and anonymously, Tor's creators opened the door to the underbelly of the Internet.
Though Tor's creators had good intentions, they could not have known the widespread impact that their invention would have on criminal activity.
The Rise of Tor

The 1960's-1990's highlighted a growing demand for both private Internet access away from the government eye and easy accessibility of any content that one desired. Tor was the answer to both these demands.
Though development of Tor began in the 1990's, it didn't fully spawn the growth of the dark web until its release in 2002.
In the 1990's, researchers David Goldschlag, Mike Reed, and Paul Syverson at the U.S. Naval Research Lab (NRL) began developing a way of routing traffic through the Internet as anonymously as possible in response to growing concern over the lack of security on the Internet.
This lack of security, in part due to how new the Internet was, created nightmares about government tracking and surveillance. Goldschlag, Reed, and Syverson aimed to route Internet traffic anonymously through multiple servers and encrypt it along the way, calling their idea "onion routing".
When Tor was released in 2002, it was purposely kept as a free and open software. This was so the software could be easily accessible to those who wanted it and so it could rely on a de-centralized network for maximum security.
As Tor gained popularity, its users started demanding that its creators address censorship by allowing those living under oppressive governments to publish their thoughts and access restricted websites freely.
This motivated Tor's creators to start developing a way for its network to get around government firewalls so its users could access government-restricted websites.
Though Tor's creators had noble intentions, seeing as they made the platform free and built it to address government censorship, they continued to run into another problem − its platform was highly complex and technical, restricting usage to mostly tech-savvy users.
This discovery led Tor's creators to begin developing a solution to Tor's accessibility issues. In 2008, a Tor browser began to be developed, which would make Tor both easily accessible and user-friendly. Once the Tor browser was released, it was only a matter of time until more and more dark websites would begin to pop up.
The Rise of the Dark Web

With the release of private browsing networks like Tor, collections of dark websites and a subsequent community of followers began to emerge in full force.
Though many dark websites were formed to help those living under oppressive governments push back against censorship, the temptation of having a corner of the Internet where you could browse anonymously fueled a rise in the number of dark websites that hosted illegal content.
2009: The Release of Bitcoin
Before cryptocurrency was invented, illegal transactions on the dark web were hard to complete, seeing as customers could potentially be located thousands of miles away and neither party wanted to risk using credit cards or PayPal for transactions because they leave paper trails.
Cryptocurrency, a form of digital currency that facilitates transactions anonymously, was the answer to this persisting problem. Though different forms of cryptocurrency had been in development since the 1990's, none stuck until 2009, when one called Bitcoin was released.
A man named Satoshi Nakamoto "mined" the first Bitcoin, effectively starting a revolution in illegal transactions online. Bitcoin solved the problem that previous versions of cryptocurrency couldn't − it had a special accounting ledger in place that prevented users from copying money.

With the issue of anonymous transactions solved, illegal sales on the dark web surged.
2010: Arab Spring
Even though the dark web saw a rise in illegal transactions in the 2010's, it served a benevolent purpose in late 2010 during the Arab Spring.
The release of the Tor browser made it more accessible to users and activists alike who needed it during this time. Tor not only protected people's identities online, but also allowed them to access critical resources, social media, and blocked websites.
2013: Silk Road Shutdown
In 2011, a Gawker-affiliated blog published an exposé on the Silk Road, a dark web marketplace that "made buying and selling illegal drugs as easy as buying used electronics." This exposé helped drive traffic straight to the Silk Road, quickly boosting its sales.
It wasn't long until the FBI caught on and started a campaign to shut it down. In 2013, the FBI successfully completed a sting and shut down the Silk Road. This was a historic sting, seeing as the Silk Road drew close to a million users at one point.
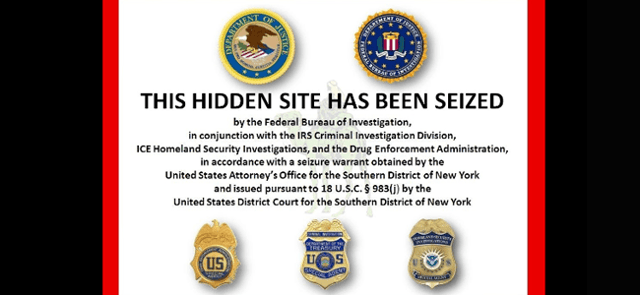
a picture of the Silk Road website following the FBI sting
The Silk Road's popularity highlights how large the demand for illegal drugs was during this time as well as how governments across the world were beginning to crack down on the dark web.
2013: Snowden Whistleblowing
Demand for tools to protect against mass surveillance became mainstream partially due to the Snowden revelations in 2013. Tor was instrumental in aiding Snowden's whistleblowing by maintaining the security of his project. This showed the extent to how iron-clad Tor's security is.
The Snowden case showed how Tor can be used for good, allowing for benevolent whistleblowing that might not have happened on the public Internet.
2015: Playpen Shutdown
Playpen, a widely used dark website for the distribution of child pornography, amassed as many as 150,000 users at one point. Thankfully, the site was shut down in 2015 following a collaborative sting effort from the FBI and related agencies in other countries.
Though the site no longer exists, its popularity shows the extent to which demand for illegal content, no matter how depraved, can exist on the dark web.
Though many other news-worthy events have taken place on the dark web over the years, including large-scale busts on other illegal marketplaces, these are some of the highlights that show how the dark web has evolved and what kind of content it hosts.
As long as there is demand for anonymity online, the dark web will be here to stay.
The Future of the Dark Web

The dark web has forever changed the face of the Internet as we know it. Though it was created out of benevolent means, the dark web has a more sinister side, which leads many to question whether or not to trust it.
The dark web has been used to fight back against government censorship and aid political activists in spreading their messages, however, many cannot help but shudder when reading about the darker corners of the dark web, which have been home to child pornography, drug sales, and other illegal content.
The future of the dark web is uncertain. As governments continue to crack down on its usage and illegal activity scares innocuous users away, we could potentially see major shifts in the dark web in the coming years.
Dark website creators hosting illegal content might password-protect their websites or restrict traffic to a list of pre-approved IP addresses in an attempt to avoid detection by the authorities.
Ransomware attacks, which are when one threatens to take advantage of your personal and financial information that they've stolen unless you pay a ransom, are facilitated by selling lists of personal data on the dark web. Moving forward, sales of personal information could increase in popularity as criminals take advantage of how potentially lucrative the sale is.
Though the dark web poses some threats to the safety of your personal data, there are a few ways you can stay protected. For instance, you can limit where your data is stored online when possible, or create passphrases instead of passwords.
All the above advice will provide you with a solid foundation with which to protect your data from criminals. If you are a business, one of the best ways to holistically protect your data is by hiring a managed IT services company to proactively monitor your network for security threats.
Protection plans include the installation and maintenance of various anti-virus and cyber security platforms, the institution of company-wide password policies, employee cyber security training, and more.
The online world changes so frequently that your company cannot afford to get left behind or be left unprotected. Establish effective network security measures in your company today so you can be protected from the cyber threats of tomorrow.
Posted by Erica Kastner

Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.


