6 MIN READ | SMALL BUSINESS CYBERSECURITY
Lately, the news seems to be flooded of reports of ransomware attacks. The Colonial Pipeline, JBS Foods, Kia Motors, and even the NBA (National Basketball Association) have all been victims of these attacks..
cybersecurity
Read More
CYBER SECURITY | 6 MIN READ
Botnets are a form of malware that poses threats to businesses and individuals alike. Keep reading to learn what a botnet is, how it works, and cyber security tips to avoid becoming a victim.
cybersecurity,
cybercrime
Read More
CYBER SECURITY | 5 MIN READ
Consistent and automated data backups are a cornerstone of efficient business operations. When your network goes down, you may have to restore it to your most recent backup to avoid any data loss. But what about when your.
Email Security,
cybersecurity
Read More
REMOTE OFFICE | 8.5 MIN READ
Once a dedicated space in your house is set aside to be turned into a home office, the complicated task of furnishing it comes next. In this article, we'll break down each piece of office equipment into low, medium, and.
cybersecurity,
remote office
Read More
MANAGED IT SERVICES | 4.5 MIN READ
Businesses looking to better secure their network may turn to either a Network Operations Center (NOC) or a Security Operations Center (SOC). However, when both sound so similar, it can be difficult to use their.
Managed IT Services,
cybersecurity,
network operations center
Read More
CYBER SECURITY | 5 MIN READ
Businesses looking for assistance managing employee network help requests may turn to a Network Operations Center. However, what are the unique benefits that of a NOC that differentiates it from a help desk? Keep reading to.
Managed IT Services,
Network Security,
cybersecurity
Read More
REMOTE WORK | 5.5 MIN READ
Your remote employees may be unknowingly putting your company's data at risk. Working from home can potentially lead to data breaches, identity fraud, and a host of other negative consequences. Keep reading to learn the top.
cybersecurity,
remote office
Read More
CYBER SECURITY | 5 MIN READ
Cyber security policies are becoming more and more common in businesses as they strive to mitigate the risk of an employee accidentally leaking sensitive data or falling for a phishing scheme. These policies need to strike a.
cybersecurity
Read More
CYBER SECURITY | 4 MIN READ
IT professionals and cyber criminals are constantly performing a sort of dance together. When cyber criminals move one way, IT professionals must move in response, and vice versa in a never-ending salsa. Since cyber criminals'.
cybersecurity
Read More
CYBER SECURITY | 6 MIN READ
Acts of Mother Nature and the wrath of cyber criminals can be unpredictable. If your business' network went down tomorrow due to a natural disaster or cyber attack, how would you ensure that business operations continue.
cybersecurity,
BCDR plan
Read More
CYBER SECURITY | 4.5 MIN READ
When most people think of the word "antivirus", they think about that software you download on your computer to keep you from being hacked. While this is true, it is a simplistic definition. Keep reading to find out what.
cybersecurity,
antivirus
Read More
CYBER SECURITY | 4 MIN READ
In today's digital age, data privacy is becoming more and more of an issue. In response to cries for consumer privacy, more laws and regulations are being passed to manage data storage and curtail data sharing by businesses.
Managed IT Services,
cybersecurity,
Managed Services Questions
Read More
CYBER SECURITY | 5 MIN READ
Business Continuity and Disaster Recovery (BCDR) plans help organizations mitigate the risks associated with network downtime and interruptions to business operations. Keep reading to learn what a BCDR plan is, how your.
cybersecurity,
small business cyber security
Read More
MANAGED IT SERVICES | 5 MIN READ
If your business is looking to improve your cyber security efforts, there will come a point in the research and decision process where you will need to figure out if you want in-house or managed IT. As a managed IT.
Managed IT Services,
cybersecurity
Read More
CYBER SECURITY | 4.5 MIN READ
Virtual Private Networks, known as VPN's, are a great asset to your business. By allowing your employees to access and share files on your network securely, you help mitigate the risk of data breaches. Keep reading to learn.
cyber security best practices,
cyber security solutions,
cybersecurity,
small business cyber security
Read More
CYBER SECURITY | 5 MIN READ
Expanding your company to multiple offices is an exciting development. When building new branches, you might not consider the necessary steps to set up your network to securely handle employees from multiple branches working.
cyber security best practices,
cyber security solutions,
cybersecurity,
small business cyber security
Read More
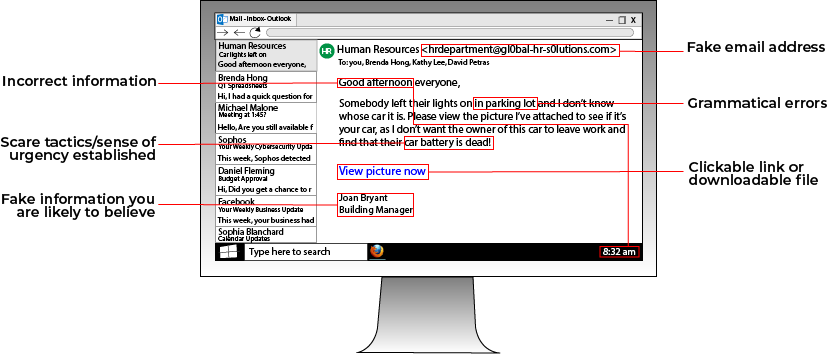
CYBER SECURITY | 5.5 MIN READ
In our rapidly changing world, it's hard to predict what somebody might have for breakfast tomorrow, let alone how ransomware will change in the coming years. Read more to learn about developing ransomware trends that could.
cybersecurity,
ransomware and phishing
Read More
CYBER SECURITY | 10.5 MIN READ
Major news outlets, from CNN to Forbes to the New York Times, have been reporting recently on the growing and shifting threat of ransomware. Just last week, the New York Times reported on the continued growth of ransomware.
cyber security best practices,
cybersecurity,
small business cyber security solutions,
ransomware and phishing
Read More
CYBER SECURITY | 7 MIN READ
If you're currently in the market for a managed services provider, you might have seen or will come across a contract spelling out your services agreement. Managed IT services contracts can come with terms that might confuse.
Managed IT Services,
cybersecurity,
Managed Services Questions,
cyber security
Read More