SOCIAL ENGINEERING | 10 MIN READ
Cyber security is becoming more and more of an issue for companies and individuals alike. With cyber attacks becoming commonplace in the news, the word "phishing" has probably come up. But what is phishing? Keep reading to learn what a phishing attack is (including its various forms) as well as tips on how to prevent it.
Not enough time? Jump to:
What is Phishing?
Phishing, a play on the word "fishing", is a cyber attack that's a form of social engineering. It involves attempts to gain access to a victim's personal accounts or capture their sensitive data by tricking them into revealing passwords or personal information. The most common form of phishing takes place over email.
Signs of a Phishing Scam

Sometimes we don't realize a phishing scam has occurred when we hear about or experience one for ourselves.
The most popular phishing scams are emails that pose as a financial institution (like a bank or the IRS). It's difficult to know if you're being scammed if the scammer sends you an email disguised with your bank's logo.
How do they know my bank's logo?
More often than not, hackers don't know your personal information, which is why email scams are so popular. Here, they choose a popular financial institution and blast their email to thousands of random people.
Their hope is to reach a handful of recipients who actually do business with that bank, making it more likely they'll click on the malicious links embedded in the email.
So what do you look for?
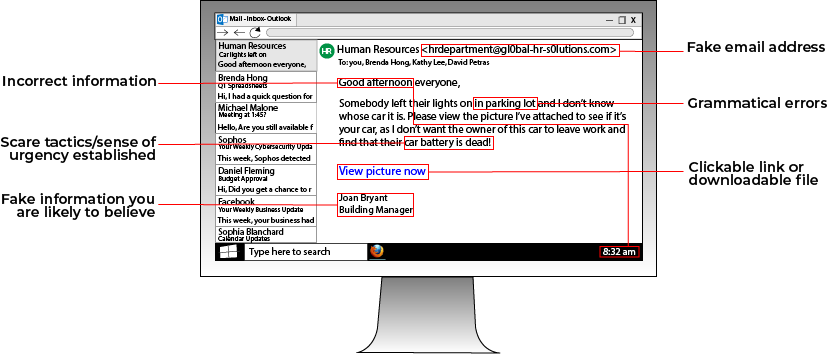
Poor Grammar/Incorrect Information: If an email doesn't read with appropriate grammar, then it most likely isn't from a professional institution. Besides misspelled words or bad grammar, look for odd information that sticks out. For instance, if you receive an email in the morning but the greeting says "Good Afternoon", that shows you that the email was likely copied and pasted or is from a different country with a different timezone.
Fake Email Addresses: If you receive an email claiming to be from an official organization, double check the sender's address. While an email may claim to be from Microsoft, if the email address is "accounts@Micr0SofT.biz-ent1" that email is likely from someone pretending to be Microsoft.
Scare Tactics: If a sense of urgency or fear is established in the email out of the blue, proceed with caution. For instance, if you randomly get an email from your bank saying that you need to immediately log into your account or your account will be deleted, that may be a phishing attempt. If an important organization such as your bank really needed to reach you for an emergency, they would exhaust other methods of contact as well, like phone calls and mail.
Random Subject: If the email you're receiving seems out of the blue, for instance a company that you haven't spoken to in years saying "Regarding Our Meeting" in the subject line, or an email from a woman you don't know sends you an email with the subject line "Urgent Action Needed", be aware. Phishing emails will try to use eye-catching subject lines to reel you in and catch you hook, line, and sinker.
If you spot just one of these tactics in an email, such as a misspelled word, that doesn't automatically mean that it is a phishing attempt, but get in the habit of looking for these common patterns in an email. You should pay special attention to emails that contain multiple warning signs.
RELATED: What is Social Engineering? Tips, Types and Prevention
Types of Phishing
There are three main types of phishing and phishing-like attacks addressed below (in order of popularity):
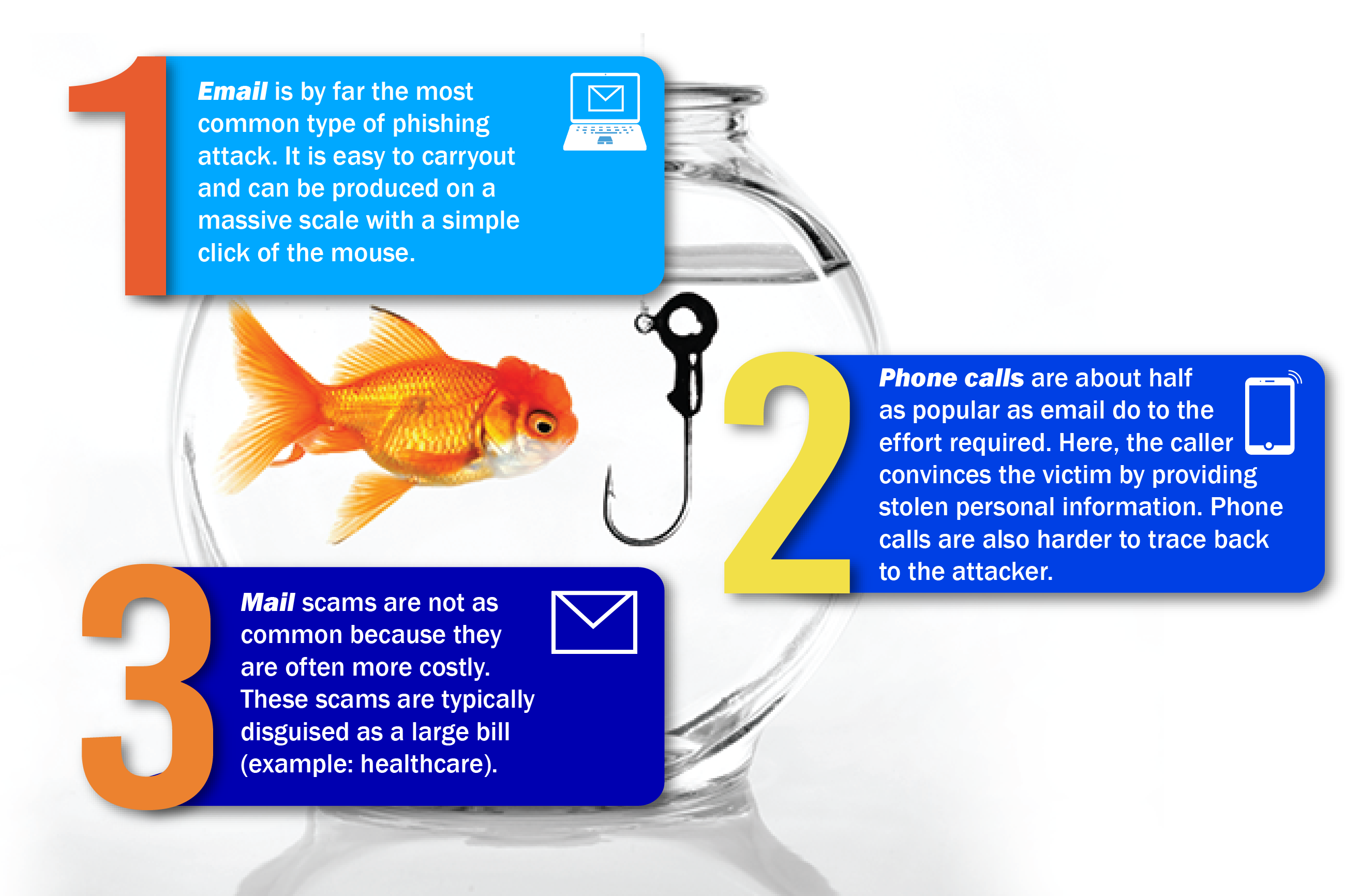
Email: Email is by far the most common type of phishing attack. It is easy to carryout and reproduced on a massive scale with a simple click of a mouse.
Phone: Phone calls are about half as popular as email. For a phone phishing attack to be carried out successfully, the person calling needs enough personal information to sound convincing to the target (you). Phone calls are also harder to trace back to the attacker, but do take more time and effort.
In recent history, a popular phishing attack was carried out by people posing as an IRS agent on the phone, threatening to garnish wages or throw people in jail if they didn't settle their tax dispute over the phone.
Mail: Mail scams are not as common because they can be the most costly to implement. These scams are typically associated with a large bill to be paid, which is why it is most common as a healthcare scam.
If you see that there isn't a return address (and you weren't expecting a bill), don't trust the source. Scams like this usually include a website or phone number you can use to make a payment (how convenient).
How to Prevent Phishing
Many phishing attempts can be thwarted by taking a few simple steps. Besides paying attention to the warning signs previously listed, take a few actions when you see suspicious emails.
Recognize the Signs
The most popular type of phishing attack takes place over email. Looking out for the warning signs in a phishing email can stop an attack in its place.
If an email has just one of these warning signs, that may not automatically mean that the email is a phishing attempt. However, be sure to look at your emails from a big-picture viewpoint to figure out the intent behind the message.
Google It
If you think a phone call or email may be a phishing attempt, consider Googling some of the information in it, such as the company, phone number, or email address.
This can lead you to forums and reports from victims and show you if the company or person contacting you is fraudulent. A great website to reference is usa.gov and its list of common types of fraud.
Don't Download or Click on Suspicious Material
As a good rule of thumb to avoid falling for phishing emails, never download an attachment or click a link from an email, especially an unknown address, unless you requested something from the sender.
If you really think the email may be safe and want to test out a link, try finding the attached page yourself on Google first.
For instance, if you receive an email claiming to be from your bank asking you to click a link and enter information, try to find that same page yourself by visiting the bank's website without clicking on the link.
If your bank's website doesn't have that page and they don't know what you're talking about when you call them, then the email may be a phishing attempt.
Businesses need to be vigilant about using personal accountability to motivate employees to protect sensitive company information. b
Using the information above is a great step. As a managed IT services provider, we unfortunately see companies and individuals alike fall for phishing traps too often.
Employee cyber security education is a crucial step in protecting your network and securing sensitive data. Phishing threats aren't going anywhere, which means that businesses must take action to avoid becoming a future victim.
RELATED: Cyber Security Solutions: 12 Best Practices for Businesses
Want to Learn More?
What is Social Engineering?
Social Engineering Techniques and Ways to Protect Your Network
What Are Whaling Social Attacks?
How Much Do Managed IT Services Cost?
Posted by Erica Kastner

Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.

