CYBER SECURITY | 5 MIN READ
Email archiving is a great way for businesses to stay compliant with data regulations, boost productivity, and more. As a Managed Service Provider, we understand how much email archiving is key in minimizing downtime when it comes to data recovery. Keep reading for a comparison of some industry leading brands.
Not enough time? Jump to:
Benefits of Email Archiving Software
How Else You Can Safeguard Your Emails
Top Brands Compared

The following comparison of top email archiving software providers Barracuda, Mimecast, and ArcTitan has been sourced from a mix of customer and third-party product reviews.
Barracuda
Pros
- Unlimited storage− This part of their offering allows businesses the flexibility to archive as many emails as they wish.
- Comprehensive audit trail− For businesses looking to use an email archiving software to stay compliant with data regulations, Barracuda's platform preserves an accurate historical email record.
Cons
- Slow to export large amounts of data− The software can get stuck sometimes when exporting a large amount of data.
- User interface−The user interface is a bit outdated, which means that end users may sometimes find the system clunky or slow.
- Customer service− Some end users say that the customer service offering is lacking and insufficient.
Mimecast
Pros
- Sandbox feature− Mimecast has a feature that allows customers to sandbox all links within emails before users are redirected to them. This can help prevent phishing schemes from being successful.
- Targeted Threat Protection (TTP)− This is a great service that proxies URL links included in emails, which helps protect against malicious attachments that could lead to ransomware.
- Easy setup− Their software requires minimal setup, letting end users get started with the product faster.
- User experience− The platform is easy to use, which streamlines processes and improves productivity.
Cons
- Learning curve for search capability− The search capability takes some time to learn.
- Limited platform integrations− Is only available as a Software-as-a-Service (SaaS) offering.
ArcTitan
Pros
- Extensive platform integrations− ArcTitan can be used on a variety of platforms, from Windows and Mac to iPads.
- Search capabilities− ArcTitan prides themselves on their software's search capabilities, which enables users to use in-depth searches manually or automatically, even allowing them to search for popular attachment types such as PDF.
Cons
- Simplistic search functionality− ArcTitan's software offers more limited search functions than other providers on this list.
- Outdated user interface− Some end users find ArcTitan's platform to be clunky and non-intuitive.
- Expensive− Small businesses in particular may find ArcTitan's offering to be a bit out of their price range.
Which One is the Best?
Any of these brands could be a good fit for your business. When evaluating various email archiving providers, look past price to really examine which features your business needs and which it simply wants. The right provider will have a healthy balance of both.
Additionally, examine their customer service offering. While a software may seem appealing, if issues arise and customer support is lacking or non-existent, that could severely hinder productivity within your business.
Benefits of Email Archiving Software
Data Security
Email archiving solutions are layered with data backup and disaster recovery capabilities. This maximizes secure long-term storage of sensitive and important information.
Archived emails are moved to a secure off-site server or cloud environment, which reduces the chances of a cyber criminal accessing these emails by hacking your office's network.
Additionally, some email archiving providers, such as the one that we partner with, sell additional email security products, which means that you can use them as a one-stop shop to maximize productivity and data security for your business.
Regulatory Compliance
Industries subject to data privacy regulatory compliance, such as the legal and healthcare industries, must follow data storage procedures to maintain compliance.
For instance, HIPAA requires those in the healthcare industry to store records for at least six years. To comply with Sarbanes Oxley in the legal industry, firms have to store records for longer.
Industries such as these can use email archiving, a long-term storage solution, to comply with data storage requirements.
Email archiving features also ensure regulatory compliance by showing a tamper-proof log of who reads which archived emails and when. Features like this can identify users who have viewed sensitive information that they shouldn't have access to, which can minimize data privacy regulatory violations.
RELATED: Can Businesses Be Sued for Data Breaches?
Productivity
Instead of wasting time searching your entire inbox, which can quickly become inefficient with the limited range of search filters available with major email providers, you can utilize email archiving to find the emails you want with ease.
Some archiving solutions come with additional email search filters such as attachment name and words within documents, which further reduces the time it takes to find emails you need.
Additionally, automated deletion of archived emails means that you no longer have to waste time going through older emails and deleting them to free up limited inbox space. Optimized email server space can improve server performance as well, since clogged servers can begin running slowly.
Minimal Downtime
As previously mentioned, email archiving can be used as a part of a holistic Backup Continuity and Disaster Recovery plan to ensure long-term storage of the emails that matter most.
However, email archiving not only assists in backup recovery but shortens the process. This is because archived data can take up less space than data backups.
Protection Against Human Error
While computers are built to be perfect, humans aren't. Emails can accidentally be deleted, and malicious actors can purposely delete sensitive or important information.
Email archiving mitigates these risks by storing important emails in another secure location.
Tamper-proof archive logs ensure that malicious actors who view sensitive archived emails are quickly identified.
How Else You Can Safeguard Your Emails
Know How to Spot a Phishing Email
Phishing emails are a cyber attack that involves attempts to gain access to a victim's personal accounts or capture their sensitive data by tricking them into revealing passwords or personal information.
While email archiving software is great for storing emails that otherwise would be automatically deleted or could get lost in your clogged inbox, it doesn't protect against malicious emails.
By training employees on how to spot a phishing email, you can prevent data breaches and ransomware attacks, therefore safeguarding company data.
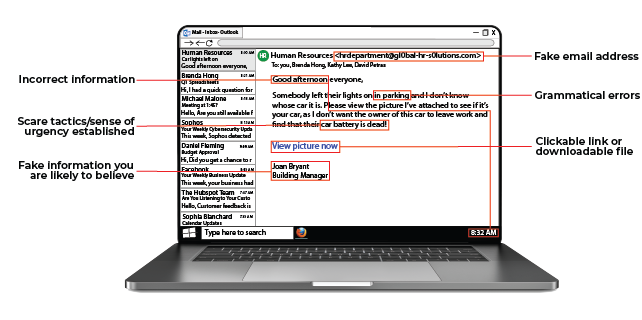
As you'll see in the graphic above, there a few red flags you can spot in an email to alert you to a possible phishing attempt. For instance, scare tactics and a sense of urgency are used to push victims into clicking on malicious links without thinking.
Emails with this sort of language should immediately be given a second read to ensure innocence. Additionally, although the email may look like it comes from someone innocuous, such as your HR department or your bank, a closer inspection of the actual email address sending you the email can reveal a possible phishing attempt.
In the example above, you'll see that although the email says it is from the company's HR department, the email address is full of grammar errors and character substitutions, which points to the address as fake.
RELATED: Spam vs. Phishing: What's the Difference?
Install Spam Filtering Software
While many email providers have built-in filters that automatically detect and remove spam emails, these filters aren't 100% accurate.
If you're in a position of power at your company, spam senders target you more than average, which means that your already full inbox will likely let through some spam emails, hindering workplace productivity.
Spam can be minimized through the use of email filtering software.
This software analyzes incoming emails for red flags that signal spam or phishing content and then automatically moves them to a separate folder. Red flags can include:
- Common trigger words that signal an unwanted email, such as "free" or "earn money"
- The sender's IP address has previously been flagged for spam
- Designs that include large images or gaudy large fonts
This software can also be used to monitor for phishing emails as well. Red flags that signal phishing emails include:
- A link or attached document is included in the email
- The sender's IP address has previously been flagged for phishing
Phishing filters will typically move flagged emails to an additional inbox, sometimes labeled as "Other". In this inbox, flagged emails will be put "on hold" until you release, block, or allow them.
If you release an email, then it is sent to your normal inbox to be opened, but in the future you will have to continue approving emails from the sender. If an email is blocked, then the email is rejected and the sender will be now be blocked from sending you future emails.
If an email is permitted, it is delivered to your normal inbox and the sender will automatically be approved to send emails directly to your inbox moving forward.
RELATED: How to Control Spam [Tips + Recommendations]
Hire Managed IT Services
As a Managed Service Provider (MSP), we understand the challenges that businesses have with securing employee email inboxes. MSP's like us can secure both your inbox and your overall network by implementing a layered cyber security solution.
We install an email security software called Mimecast to secure our clients' inboxes. From there, we can install a host of other software such as antivirus and anti-ransomware to keep all cyber threats at bay, and then monitor for any other threats that slip through.
RELATED: What are Managed IT Services?
Implementing an email archiving software in your organization is a great step towards email security and business productivity.
For more office technology content, follow our blog!
Posted by
Tech Support