
SOCIAL ENGINEERING | 5 MIN READ
Victims of social engineering attacks can have their personal information stolen from right under their nose without ever knowing. Social engineering attacks are crafted around two basic tenants of human psychology: fear and the need to be helpful. These attacks trick victims into revealing personal information such as account logins that can then be used to inflict personal or financial damage. Keep reading to see what social engineering trends we predict will continue to grow in the coming years.
Not enough time? Jump to:
How to Avoid Social Engineering Schemes
What Is Social Engineering?

In simple terms, social engineering relies on deception to trick a victim into clicking a link or downloading a file that then lets a hacker steal personal information or hack an account.
For instance, you could receive an email appearing to be from your bank telling you that you need to click a link to log into your account immediately to update some important information or you'll temporarily lose access.
However, the email is actually from a hacker pretending to be your bank, and the link leads to a fake website that stores the credentials you provide and uses them to hack your bank account.
Some confuse social engineering with ransomware, but the two are different. Ransomware is a type of malware that encrypts your files, making them inaccessible unless you pay a ransom to the hacker. And unlike social engineering, ransomware doesn't have to rely on trickery to harm a victim.
A hacker can gain access to a victim's network through many other avenues, whether it's figuring out weak passwords or finding security gaps in their network.
However, once a hacker gains access to a victim's computer, whether it's through a social engineering scheme or another tactic, the outcome can have dangerous consequences for the victim.
RELATED: How Does Ransomware Work? [Infographic]
Personalized Attacks
While social media has made it easier for us to stay connected and share our lives with each other, the constant sharing of personal information lends opportunities to cyber attackers.
For instance, all the personal information that one shares on social media, such as their kid's names and their childhood memories, is common information used in account logins.
A hacker looking to access someone's personal or business accounts could stalk their social media profiles and use the personal information they find to craft phishing emails or phone scams.
When creating and posting on social media accounts, always set your accounts to private and do not accept friend requests from those you don't know.
Deepfakes

Deepfake technology is a growing concern in the cyber security industry. It involves a combination of machine learning and artificial intelligence to edit a photo, video, or voice clip with malevolent intent. This media is then used to trick victims into handing over personal information.
The trend, which first started gaining ground in 2017, started off as a way for people to edit celebrities and other people's faces onto sexually explicit videos so it looks like those people were the ones in the video.
With the 2020 presidential election coming up, some are concerned that deepfakes can be used to manipulate political images and videos to the editor's liking. This growing trend makes cyber security experts worry about how deepfakes can be used to persuade victims into handing over their personal information.
For instance, a victim could be emailed a video that looks like it's from their IT manager asking for their account login for routine maintenance. Or, a victim could be emailed a link to join a remote conference with a co-worker or client, but in reality the person they're talking to and discussing personal information with is an edited face.
Deepfake social engineering attacks are already being reported − the Wall Street Journal reported on a CEO scammed out of a quarter of a million dollars over a voice scam.
While the future of how deepfakes will be used is uncertain, the possibility is there for the technology to be used to carry out social engineering attacks and steal victims' personal information.
SIM Swapping
Enabling two-factor authentication whenever possible is one of the top-rated cyber security tips from leading industry experts. However, a growing trend called "SIM swapping" is rendering this security tactic useless.
SIM swapping is a social engineering tactic that gains access to a victim's accounts that are protected by two-factor authentication by tricking them into providing the one-time passcode sent to their phone. Once the passcode is given, the attacker can use it to their advantage to receive all texts and calls intended for the victim.
This allows the attacker to receive all passwords for account logins and break into a victim's personal accounts. While you should still enable two-factor authentication whenever possible, be extra diligent about paying attention to the websites you use to log into personal accounts.
How to Avoid Social Engineering Schemes
While social engineering schemes are becoming more targeted and are evolving to take advantage of emerging technology, there are a few ways you can be diligent and stay one step ahead.
If you are a business, you can use educational cyber security programs to train employees on ways to avoid common social engineering schemes as well as how to create secure account logins that are hard to crack. You can even send out fake phishing emails within your company and send those who fall for them to a cyber security seminar.
Educational cyber security programs also foster a culture of personal accountability within your organization as it highlights how just one instance of human error can potentially compromise a business' entire network.
Social engineering attacks are commonly carried out through phishing emails. The graphic below highlights a few tips on how to detect phishing emails and stop them in their tracks.
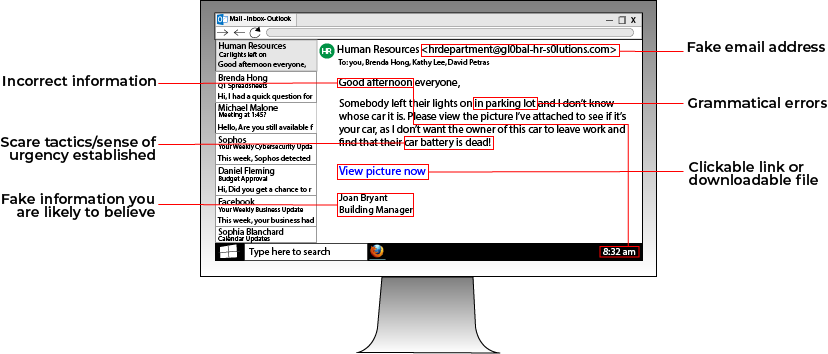
While this graphic won't with 100% certainty prevent you from falling for a phishing scheme, it shows common themes you can look for when receiving emails, especially those that originate from outside your company.
There are a few additional general tips you can follow to avoid falling for social engineering schemes:
- Pause. Before opening an email or clicking a link on a website, examine the source and its intentions. For instance, if you're on a website and are about to log into a personal account, double check the URL and make sure that you're actually on the correct website and not a fake one designed to resemble the real thing.
- When in doubt, copy and paste links. If you see a link from a source that seems a little untrustworthy, copy and paste it into a search engine. If it shows up in the search results and seems legitimate, then you know the link won't download malware on your computer.
- Be cautious about downloads. If an email coming from an external source or a website asks you to download something, be extra cautious. Hackers can easily manipulate download links to install malware on your computer.
- Be wary about messages and links that instill a sense of urgency or fear in you. When we are afraid or feel pressured to make a decision, we don't always think clearly. Hackers use these psychological tricks to carry out social engineering attacks. For instance, if an email tells you to click on a link right now to change your password or you'll permanently lose access to your account, that may be a social engineering scheme at work.
Shifting your cyber security strategy in response to emerging social engineering trends will help place additional barriers to entry between your network and a cyber attacker.
As a Managed Service Provider, we understand the risks associated with social engineering attacks. We ensure that our clients' networks are up-to-date and all employees are educated on how to detect and avoid common schemes.
While the exact future of social engineering is uncertain, one thing is clear − it is here to stay, it is constantly evolving, and if you don't adapt your network strategy to keep up, you put yourself at risk of becoming a victim.
Posted by Erica Kastner

Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.

