CYBER SECURITY | 6 MIN READ
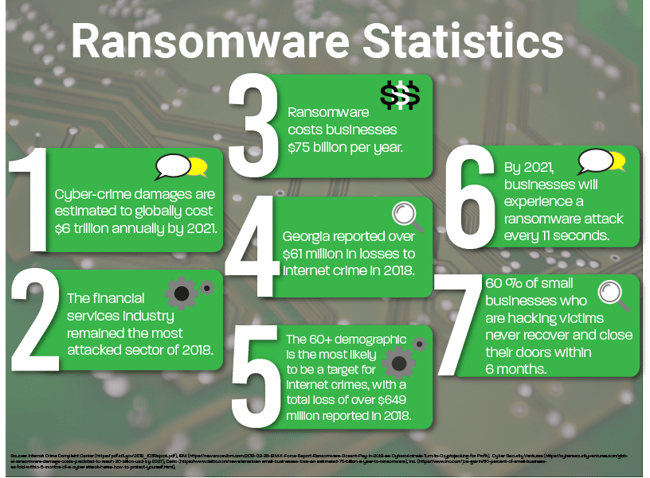
In our increasingly inter-connected world, more and more people are using computer systems that host vital private files, from bank statements to tax documents with social security forms to HIPAA-sealed medical records. These files serve as bait to attract swarms of hackers who know that their victims are willing to pay a price to keep them. Take Texas as an example of the massive scale with which these incidents can take place. Just recently, the data of 22 Texas local government agencies was stolen and held for ransom, according to US News and World Report.
Today, hackers use incredibly sophisticated methods to collect information without your permission. Ransomware threats, dating back to around 2012, have been steadily growing since and show no signs of slowing down. According to the Internet Crime Complaint Center’s 2018 report, Georgia ranks among the top 10 states with the most internet crime victims, and could potentially move up the list in the future.
So, how does ransomware work and what does it look like? We help companies every day with ransomware protection, so we are intimately familiar with how ransomware works and what it looks like.
Unfortunately, once you have been hit with ransomware, the outlook can be bleak. 60% of all small businesses who are victims of hacking never recover and close their doors within 6 months of an attack. To better understand ransomware, we need to first understand the threats that make our personal data vulnerable.
Not a lot of time? Jump to:
How Does a Ransomware Attack Work?
What Does Ransomware Look Like?
How Can Ransomware Be Prevented?
How Does a Ransomware Attack Work?
Ransomware is exactly what it sounds like – a form of malware (malicious software) that encrypts personal or company data and threatens to publish, destroy or sell it if the hacker’s monetary demands are not met.
If that doesn’t scare you, this might - from 2014-2018, the Internet Crime Complaint Center reported $7.45 billion in losses to Internet scams.
Phishing is the fraudulent practice of calling victims or sending ransomware-filled emails posing as a reputable entity - usually a financial institution - to encourage a victim to willingly reveal their personal or company’s information.
How does ransomware infect a computer?
Hackers create an email that is designed to look identical to the company it is misrepresenting. The email contains a link, and from there one of two scenarios can happen. The first scenario involves the email link directing a user to a “secure” web page that will then ask for personal information.
Once this information is provided, the hacker gains entry to a computer system, infects it with ransomware, encrypts all valuable documents, and holds them for ransom.
The second scenario involves the email link leading a victim to a download. Sometimes, this link downloads a Trojan virus onto a computer, which opens a door that a hacker can use to infect a system with ransomware.
Other times, the link downloads ransomware directly onto a computer. Once the hacker gains entry to a system, he/she then encrypts all valuable files and holds them for ransom.
RELATED: Ransomware vs. Social Engineering: What's the Difference?
What Does Ransomware Look Like?
The following content showcases a taste of what one’s computer screen can look like when the computer becomes infected with ransomware.
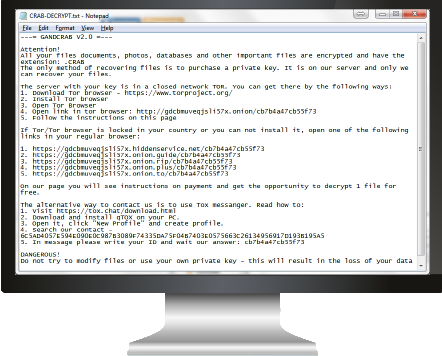
GandCrab
First reported in January 2018, this type of ransomware has only gained notoriety since. GandCrab ransomware attacks individuals instead of businesses by primarily utilizing phishing tactics to find its victims.
GandCrab’s creators have continued to remain a threat by constantly updating their code and adapting to security developments.
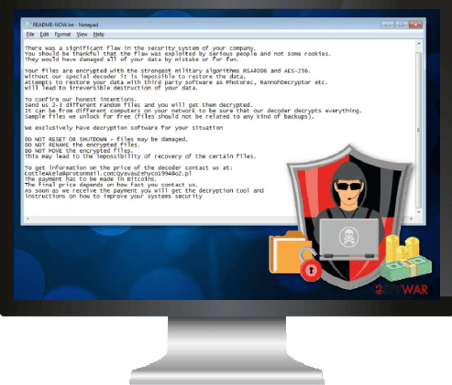
LockerGoga
One of the more recently widespread types of ransomware, LockerGoga gained notoriety in early 2019 when it attacked both French engineering consulting company Altran Technologies as well as Norwegian aluminum manufacturing company Norsk Hydro.
LockerGoga infects systems by gaining security credentials from a victim through phishing or malware infections, locking the victim out of their computer, encrypting files, and leaving a ransom note.
Digitally signing the code with valid certificates has helped LockerGoga sneak into computer systems.
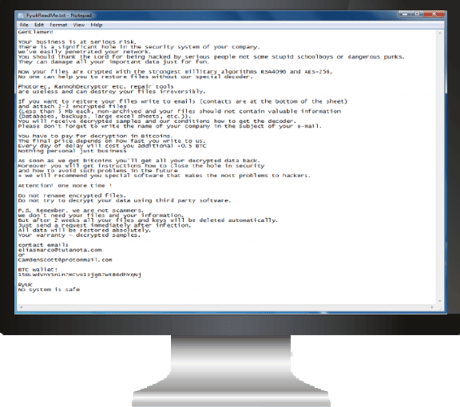
Ryuk
Ryuk made its debut in August 2018 and has siphoned over $3 billion since then. It uses “big game hunting”techniques by targeting large organizations for expensive ransoms.
Ryuk distributes a program called Trickbot through massive email spam campaigns and exploit kits that then find the credentials necessary to compromise systems.
Since the encryption code only infects crucial assets, this means that thorough network research takes place before attacks are carried out.
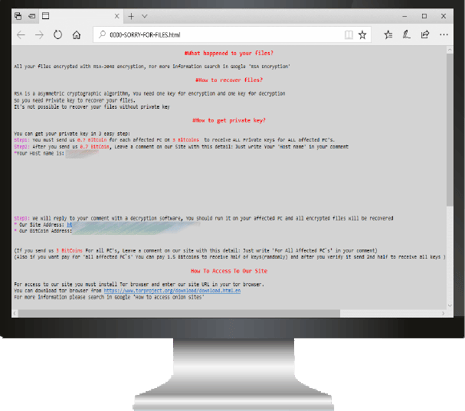
SamSam
Though SamSam has been around since 2015, it gained national notoriety by wreaking havoc on the City of Atlanta in March of 2018. SamSam uses either vulnerabilities in computers and web servers or targeted attempts to unveil weak passwords to gain access to a victim’s network.
Once a computer is infected and encrypted so files cannot be accessed, a ransom note is left that directs victims to a hidden service site, where they can pay the ransom in Bitcoin before their files are unlocked.
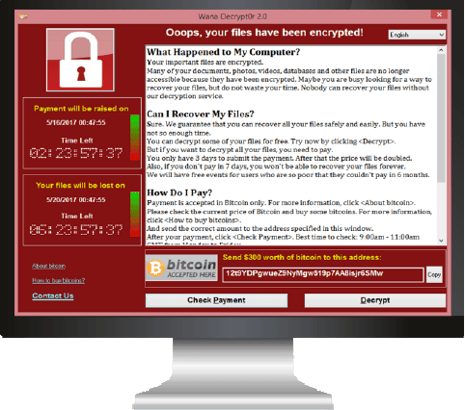
WannaCry
As of this article’s publish date, this form of malware is still targeting organizations across the globe. The attack works by using a flaw in Windows' server message block (SMB) protocol, allowing nefarious packets to enter a machine undetected.
Big-name corporations such as Boeing, FedEx, Honda and various state governments in India have been hit by the malware.
RELATED: How Ransomware Has Evolved
How Can Ransomware Be Prevented?
There is new technology available, such as Sophos' Intercept X that will stop ransomware in real-time and avoid the encryption of data.
Additionally, data back-up through a managed IT services provider (MSP) can virtually back-up your sensitive information in the cloud so that if a breach were to happen, your company would be protected.
If you don’t have the resources necessary to do the above suggestions, but still want to stay as protected as possible, make sure to diligently educate employees on the hazards of the internet – especially phishing.
There are companies that offer phishing education services. Random phishing-test emails are sent to employees, and if an employee clicks on a phishing-test email, they are enrolled in a course that will better educate them on the threats of the internet as well as cyber security best practices (including best practices for ransomware).
This “penalty” for clicking on a fake scam email is a much preferable alternative to an employee clicking on a live email that cripples the entire business.
RELATED: Here’s Why Your Employees Are a Major Security Threat

Invest in cyber security insurance.
Cyber security insurance protects a company financially if they are attacked by a hacker and incur financial loss. However, keep in mind that cyber security insurance is costlier the less protected you are (or impossible to obtain if you aren’t protected at all).
It is also costlier once you have been attacked, and the likelihood of a repeat attack is high.
So, what can be done?
For the cost of an $8-$14 per hour position at your company, you can receive the support of an entire IT team through a managed IT services provider. If they are a quality provider, they will have solutions that will keep your network from harm and assume all the risk for you.
The only real question you must ask yourself is: “Is my business worth the investment?”
Want to Learn More?
Superior Solutions - for IT on a Budget
How Much Do Managed IT Services Cost?
The True Cost of Downtime
Why Small Businesses Are More Prone to Cyber Attacks
Posted by Erica Kastner

Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.



