SOCIAL ENGINEERING | 4.5 MIN READ
Social engineering threatens your business' livelihood. By preying on human emotion to access sensitive information and hack your network, social engineering can cause a host of negative consequences. Read more to find out what a few common social engineering tactics are and how you can protect your business from falling for one.
Not enough time? Jump to:
Phishing
The most common form of social engineering is phishing. Hackers create legitimate-looking emails that seem to come from a trusted source, like Amazon, a co-worker, or your bank. The catch is that, hidden innocuously within the email, there is a link to malware.

When a victim clicks one of these links, malware is downloaded onto their computer, which either renders their computer useless, or, the victim's valuable files are encrypted and held for ransom, which then falls into the category of ransomware.
Pay close attention to your gut feeling when reading emails - if something seems off in an email, there is a chance it could be a phishing attempt.
RELATED: Phishing Tips - A Simple Guide to Avoid Malicious Emails
Baiting

Hackers know that human curiosity can be leveraged in their favor, which is why they use baiting as a tactic to gain access to a victim's network.
Imagine that you walk up to your office's copier and discover a flash drive sitting on it. Knowing that the flash drive might contain important information that the owner needs, you don't think twice about plugging it into your computer to find out who it belongs to.
Little do you know that this particular flash drive is loaded with malware, so once you plug it into your computer, malware begins to infect it, encrypting your files and putting your company's entire network at risk.
Hackers conduct on-premise attacks in other simple ways too. A hacker could also gain access to your network or sensitive information simply by pretending to be a visitor to your office.
If they're wandering around your office, most likely nobody will truly interrogate them on their presence in order to maintain a polite attitude.
This situation gives a hacker easy access to the files and devices on your network. Once inside the building, a hacker can do any number of things, like read private documents, stick a malware-loaded flash drive into a computer, or hunt for random passwords written down on sticky notes.
Phone Scams
Though it sounds cliché and outdated, criminals can successfully steal your valuable information over the phone. There are so many types of phone scams out there that it can be overwhelming to even picture what one could sound like.
For phone scams involving your company, criminals can call your company posing as a current client or your company's bank, for instance, and then ask you to reveal sensitive information such as account passwords or company credit card numbers.
Without the proper training, employees can easily fall for these tricks, which puts your company at risk of being hacked or having your sensitive information stolen.
How Can I Protect My Company?
Luckily, there are a few ways you can easily protect your business from social engineering attacks.
How to Prevent Phishing Attacks
For starters, there are a few easy ways to spot a phishing email and stop it in its tracks.
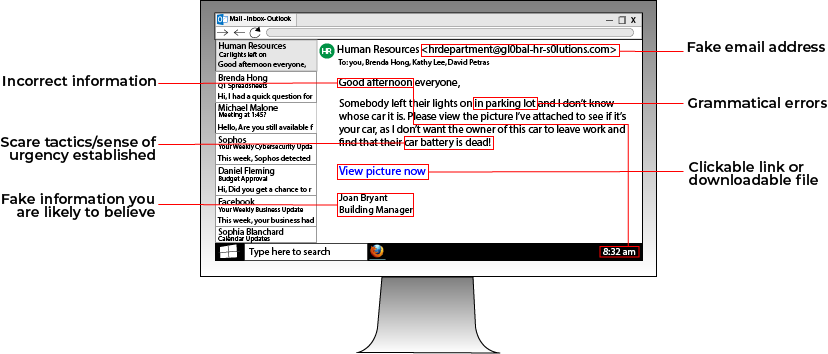
If you notice some of the red flags noted above, delete the email or report it to your system administrator.
How to Prevent Baiting/On-Premise Attacks
To prevent baiting/on-premise attacks, set simple company policies in place that instruct employees on what not to do in the event that they find an unattended flash drive or see a stranger roaming the building.
For instance, your policy could include telling employees that if they find a flash drive, send an email to the company telling everyone what you found and where you found it. Simply leaving the flash drive where it is risks another curious employee taking and using it instead.
In the event that an employee sees a stranger roaming around the building, you can instruct employees to politely ask that person if they need help finding something, and offer to direct them to the appropriate person.
If that person doesn't know where they are going or seem suspicious, then a manager or security personnel can be notified. In-person social engineering plays off social cues, which means people feel more obligated to drop standard security protocols. Educating employees on how to properly assess a situation can prevent your company from having sensitive information stolen.
How to Prevent Phone Scams
To prevent your staff from falling for a phone-based social engineering attack, establish procedures that help your staff determine what can and cannot be said or done over the phone.
For example, use your policy to answer questions such as "Should clients be required to repeat a designated passphrase to request changes to their account?" Small adjustments like this can save your business from a world of hurt.
On top of setting new security policies and procedures, consequences for failure to follow policies are recommended, too. Without consequences, employees can easily slip back into old habits.
As a managed IT services company, we know the cyber threats that companies are exposed to every day. Your employees are your greatest weakness when it comes to your network's security, so tactics like cyber security awareness training are key. Setting the right security policies in place ensures that your company won't be the next cyber attack victim that ends up on the local news.
RELATED: Cyber Security Awareness Training for Employees [Tips]
Posted by Erica Kastner

Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.

