© Standard Office Systems
© Standard Office Systems

The Boogeyman. Slenderman. The dark web. Though these all sound like scary stories dramatically spun by children at sleepovers, only one of the three is actually real.
Mystery shrouds the dark web, partially because, like the cloud, its concept sounds so vague that many cannot comprehend how it works. This mysteriousness poses a problem to those looking to improve their cyber security efforts.
If you cannot understand what the dark web is and how it poses threats, then how do you protect yourself?
As a metro-Atlanta based Managed Service Provider, we protect clients' data from being published to the dark web. We used our dark web expertise to create this definitive guide in the hopes of debunking common misinformation and educating our audience about how to protect themselves from dark web threats.
Read our definitive guide to the dark web so you know how to stay protected from increasingly tech-savvy hackers and cyber criminals.
What Is the Dark Web?
History of the Dark Web
Dark Web vs. Deep Web
Common Dark Web Myths Debunked
How Hackers Get Your Personal Information
How Hackers Pose a Threat
The Future of the Dark Web
How to Keep Your Information Off the Dark Web

Since there are various encryption tools, visitors to the site have to use the same encryption tool as the site, and most importantly know where to find the site, in order to type in the URL and access it.
Tor, now one of the main access points for the dark web, is popular because it can hide the IP addresses of its users.
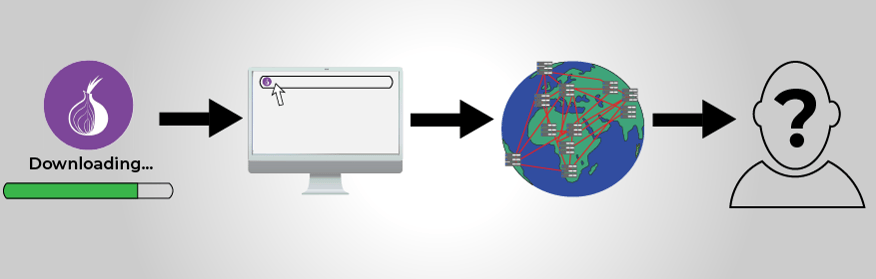
When a user attempts to access a website using Tor, Tor bounces the request for site access to multiple computers worldwide that are maintained by volunteers.
As the request bounces around computers, the site access request is encrypted and decrypted, which means that by the time the request is processed and a user accesses the website, nobody can tell where the request came from.
This bouncing method ensures that the user's IP address, which shows their geographic location, remains anonymous.

Tor does have benevolent uses. People who live under oppressive regimes that control Internet access could use Tor to access basic blocked sites or ask for help. This could be especially useful for journalists trying to break important stories to the outside world.
Though Tor was created with good intentions, it wasn't long before people found a way to use it for more sinister purposes. Since Tor hides the location of the user, it makes tracking that user difficult.
This creates an opportunity for people to create illegal websites on the dark web using Tor to hide the locations of both their operations and their customers.
Though the dark web can be used by people living under totalitarian rule to act as whistleblowers, by some estimates, over 50% of the sites on the dark web are used for criminal activities.
One of the most prevalent uses of the dark web is buying and selling illegal goods such as recreational drugs, weapons, and fake identities.
The proliferation of cryptocurrency, which are anonymous forms of digital currency, has facilitated these sales. One cryptocurrency in particular named Bitcoin is especially prevalent on the dark web.
To the average person, the dark web's most direct threat to them is the sale of their personal information. Hackers steal information from businesses or personal devices that can range from account passwords to social security numbers.
For more information, check out our article : What is the Dark Web? [Info + Tips]
Though the dark web seems like an invention of the new millennium, its history dates back farther than one might think. A few pioneers built the dark web into what it is today, a hidden underbelly of the Internet with content ranging from innocuous to downright illegal. Keep reading to learn the history of the dark web and how it has shaped the Internet as we know it.
If you want a quick summary of the main events that culminated in the formation and development of the dark web before reading the rest of this article, take a look at the timeline below.
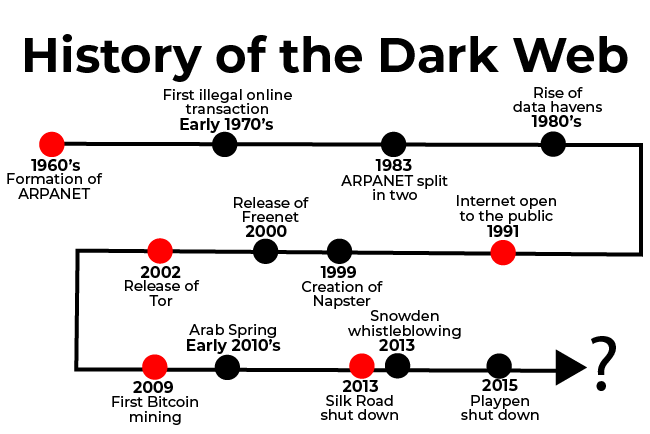 Early Days
Early DaysThe idea of an anonymous online communications network, which is the core of what the dark web is, stretches back all the way to the 1960's with the creation of ARPANET.

ARPANET, also known as the Advanced Research Projects Agency Network, was an experimental computer network created in the 1960's that was the forerunner of the Internet and later on, the dark web.
The idea for ARPANET arose from a desire to share information over great distances without the need for phone connections between each computer on a network. ARPANET was a computer communications system that later took on a tentacle-like structure that made communicating between devices possible.
Though ARPANET started out as an invention for the world of academia, the military, who was dealing with the Cold War during this time, quickly found use for it.
The Advanced Research Projects Agency (ARPA), an arm of the U.S. Defense Department, sought a computer-based communications system without a central core, which would protect against enemies attempting to black out entire networks by simply destroying its core.
This led ARPA to start funding ARPANET in the hopes that it could be used to link computers at Pentagon-funded research institutions over telephone lines.
Even though ARPANET became more privatized by the government over the years, they still let researchers, who primarily worked in universities around the country, have the freedom to try radical experiments. This can be seen in the facilitation of the first illegal online transaction using ARPANET in the early 1970's.
Stanford students used ARPANET accounts at Stanford University's Artificial Intelligence Laboratory to engage in a commercial transaction of marijuana with their counterparts at MIT.
Though ARPANET researchers had the freedom to try bold experiments such as this one, it still had strong ties to the government. This led ARPANET's founders, in 1983, to split ARPANET into two parts: MILNET, to be used by military and defense agencies, and a civilian version of ARPANET. The civilian version formed the basis for what later became the Internet.
At their core, both the dark web and ARPANET are rooted in the same desire for secure correspondence. That's why it's no surprise that the dark web began to take shape just a few decades later.
The 1990's is known as the decade of the Internet boom and the Dot-Com Bubble. In August of 1991, the Internet finally became publicly available. It was such a revolutionary concept at the time that millions of early adopters began flocking online to try it out for themselves. 
CD's, the music consumption method of choice in the 90's, along with the release of MP3 compression formats, allowed people to easily begin to illegally rip CD's.
It wasn't long until illegally ripped music made its way online to forums, and later, to a music sharing site called Napster. The meteoric growth of Napster at the turn of the millennium highlighted the increasing demand for products sold online, as it was easy and convenient.
As people began to realize that the Internet could be a one-stop shop to get whatever they wanted whenever they wanted, it was only a matter of time until more illegal transactions started happening online.
As a side note, the 1990's were also when Tor, a private Internet browsing network that would later serve as a main connecting point to the dark web, was in its early developmental stages.
In conversations about the history of the dark web, we cannot leave out Tor, which was instrumental in creating a home for the dark web.
In 2002, Tor, a private Internet browsing network, was finally released to the world. Tor forever changed the face of the Internet. By creating an environment in which people could browse online freely and anonymously, Tor's creators opened the door to the underbelly of the Internet.
Though Tor's creators had good intentions, they could not have known the widespread impact that their invention would have on criminal activity.

The 1960's-1990's highlighted a growing demand for both private Internet access away from the government eye and easy accessibility of any content that one desired. Tor was the answer to both these demands.
Though development of Tor began in the 1990's, it didn't fully spawn the growth of the dark web until its release in 2002.
In the 1990's, researchers David Goldschlag, Mike Reed, and Paul Syverson at the U.S. Naval Research Lab (NRL) began developing a way of routing traffic through the Internet as anonymously as possible in response to growing concern over the lack of security on the Internet.
This lack of security, in part due to how new the Internet was, created nightmares about government tracking and surveillance. Goldschlag, Reed, and Syverson aimed to route Internet traffic anonymously through multiple servers and encrypt it along the way, calling their idea "onion routing".
When Tor was released in 2002, it was purposely kept as a free and open software. This was so the software could be easily accessible to those who wanted it and so it could rely on a de-centralized network for maximum security.
As Tor gained popularity, its users started demanding that its creators address censorship by allowing those living under oppressive governments to publish their thoughts and access restricted websites freely.
This motivated Tor's creators to start developing a way for its network to get around government firewalls so its users could access government-restricted websites.
Though Tor's creators had noble intentions, seeing as they made the platform free and built it to address government censorship, they continued to run into another problem − its platform was highly complex and technical, restricting usage to mostly tech-savvy users.
This discovery led Tor's creators to begin developing a solution to Tor's accessibility issues. In 2008, a Tor browser began to be developed, which would make Tor both easily accessible and user-friendly. Once the Tor browser was released, it was only a matter of time until more and more dark websites would begin to pop up.

With the release of private browsing networks like Tor, collections of dark websites and a subsequent community of followers began to emerge in full force.
Though many dark websites were formed to help those living under oppressive governments push back against censorship, the temptation of having a corner of the Internet where you could browse anonymously fueled a rise in the number of dark websites that hosted illegal content.
Before cryptocurrency was invented, illegal transactions on the dark web were hard to complete, seeing as customers could potentially be located thousands of miles away and neither party wanted to risk using credit cards or PayPal for transactions because they leave paper trails.
Cryptocurrency, a form of digital currency that facilitates transactions anonymously, was the answer to this persisting problem. Though different forms of cryptocurrency had been in development since the 1990's, none stuck until 2009, when one called Bitcoin was released.
A man named Satoshi Nakamoto "mined" the first Bitcoin, effectively starting a revolution in illegal transactions online. Bitcoin solved the problem that previous versions of cryptocurrency couldn't − it had a special accounting ledger in place that prevented users from copying money.

With the issue of anonymous transactions solved, illegal sales on the dark web surged.
In 2011, a Gawker-affiliated blog published an exposé on the Silk Road, a dark web marketplace that "made buying and selling illegal drugs as easy as buying used electronics." This exposé helped drive traffic straight to the Silk Road, quickly boosting its sales.
It wasn't long until the FBI caught on and started a campaign to shut it down. In 2013, the FBI successfully completed a sting and shut down the Silk Road. This was a historic sting, seeing as the Silk Road drew close to a million users at one point.

a sample page from the Silk Road website following the FBI sting
The Silk Road's popularity highlights how large the demand for illegal drugs was during this time as well as how governments across the world were beginning to crack down on the dark web.
Playpen, a widely used dark website for the distribution of child pornography, amassed as many as 150,000 users at one point. Thankfully, the site was shut down in 2015 following a collaborative sting effort from the FBI and related agencies in other countries.
Though the site no longer exists, its popularity shows the extent to which demand for illegal content, no matter how depraved, can exist on the dark web.
Though many other news-worthy events have taken place on the dark web over the years, these are some of the highlights that show how the dark web has evolved and what kind of content it hosts. As long as there is demand for anonymity online, the dark web will be here to stay.
For more information, check out our article: History of the Dark Web [Timeline]
Imagine the Internet as an onion, with layers upon layers. The outermost layers are the easiest to access, and as you peel back the layers, it becomes harder and harder to do so.

If the outermost layer is the publicly accessible Internet that we all know and love, then the deep web is the second layer, which is hidden beneath the surface of the public Internet and is comprised of most web pages.
This is where the confusion between the deep web and dark web arises for most people. You'll see news stations spouting statistics like "96% of the Internet is the dark web and is largely inaccessible to the public".
These news stations fail to realize that that fact actually applies to the much more innocuous deep web.
The deep web is less scary than it sounds. The deep web makes up a majority of the Internet because it is all the content you can't find on search engines, such as a corporation's private database or a company's internal website pages.
A thin layer of security protects the public from accessing deep web content. Consider all the different accounts that you seek to keep private, such as your online banking account or your email.
These websites need to have privacy restrictions for a reason, which is why you can't Google and access somebody's bank account. These protected pages would be considered part of the deep web because search engines don't index them, therefore "hiding" them from most of the public.
For instance, if I am in my online banking portal, I can see a URL at the top of the page. However, if I gave you the URL to my portal, you couldn't paste it and access my account. You have to also have my account credentials to access my banking, which serves as an added security layer.
Websites purposely don’t index these pages for Google to find because only certain people should have access to them.
As for the size of the deep web, according to a study, it is actually 400-550 times bigger than the public Internet.
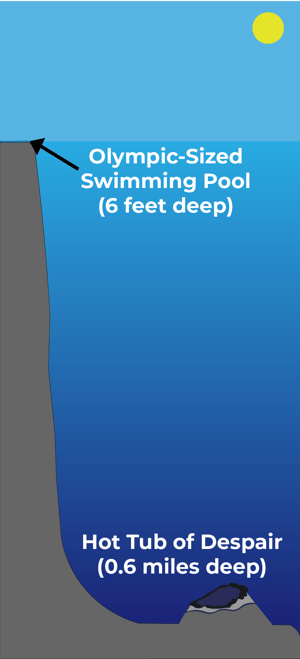
Imagine that, to access the entirety of the public Internet, you would have to swim down to the bottom of an Olympic-sized swimming pool, which is around six feet.
Now imagine that to reach the entire deep web, you would have to swim down in the Gulf of Mexico to reach the Hot Tub of Despair, a pit of extra-salty water and dissolved methane that kills any critter unlucky enough to fall inside.
You would have to swim down over half a mile (0.6 miles to be exact) to reach the Hot Tub of Despair, a depth inaccessible by scuba divers.
To put this size difference in a different perspective, this means that when someone is searching on the Internet, they are only accessing 0.03% — or one in 3,000 — of the pages available to them.
For every website, there are many more web pages on the deep web. For instance, consider any password-protected websites such as Wells Fargo's online banking portal.
Once a user logs into their bank account, all of the protected pages they can access, such as their checking account information or bank statement, are on the deep web because search engines cannot access these pages.
Keep in mind however, that for protected websites like online banking portals, even if a company has millions of users on its site, that doesn't mean that each user creates unique deep web pages.
For instance, the Wells Fargo checking account page would be a single page on the deep web, and the numbers on that page change based on the user who logs in and looks at that page.
Although there are many pages and websites on the deep web, relatively little are used for illegal purposes.
The darknet is another term that gets thrown around when talking about the dark web, so it would be wrong for us to define the dark web without talking about it.
The darknet is simply the service that hosts dark web pages and services.
The darknet and dark web comprise the most internal layer of the "onion". The dark web is technically a subset of the deep web because it too, isn't publicly accessible. According to Wired, only about 0.01% of the deep web is the dark web.
While some deep web sites can be accessed through private browsers such as Tor, the only way to access the dark web is through these kinds of browsers.
The dark web is hidden from public view in a few ways. First, since Google doesn't index for dark web sites, you can't find any by using a search engine. Just to open a dark web site, you have to use a special browser.
For some particularly secretive sites on the dark web, website owners might restrict the IP addresses that are allowed to access the site.
Though you could theoretically take the same action with a public Internet site, there isn't as much of a reason to do so as with a dark website.
For more information, check out our article: Dark Web vs. Deep Web: What's the Difference?
Many myths surrounding the dark web are perpetuated, especially by the media. However, not all of them are true. Let's separate dark web fact from fiction.

If you're already on an FBI watch list, then maybe you shouldn't go on the dark web, but for everyone else, it isn't inherently illegal to go on the dark web if you keep in mind a few points.
As previously stated, people use the dark web to view and publish content not permissible by their government. A US journalist may not be able to publish content through normal means, if staying in a foreign country on assignment.
Publishing said content isn't illegal in the US, but it is in that country. The dark web would be helpful in this scenario by protecting the right to freedom of speech.
However, even if you simply view some illegal content on the dark web, keep in mind that you never know which websites the FBI is tracking. So, although you might be okay if you visit some of the darker content, you also might be exposing yourself to an undercover FBI sting.
The dark web is frequently characterized as a hotbed for illegal activity. While it does attract criminals who sell drugs or are human traffickers, online illegal activity isn't restricted to just the dark web.
There have been many publicly accessible websites that have been shut down for producing/distributing illegal content. For instance, a 2014 Internet Watch Foundation report showcased how law enforcement found 31,266 URLs that contained images of child porn. Of those URLs, only 51 of them, the equivalent of 0.2 percent, were hosted on the dark web.
However, while illegal activity takes place on both the surface web and dark web, the dark web's ability to conceal the IP addresses of its users makes concealing and carrying out illegal activity easier.

Although the dark web is known for harboring illegal activity, just because you can access the dark web doesn't necessarily mean you can access all of its sites.
For dark website creators who really want to restrict site access, they might password-protect their site or only allow those from a list of certain IP addresses to have access.
For more information, check out our article "6 Common Dark Web Myths Debunked"

There are a few ways that hackers can get your private information. While hackers sometimes use highly sophisticated methods to obtain your private information, sometimes it's as simple as exploiting human error.
Social engineering schemes are the most commonly used hacking method. According to dictionary.com, social engineering schemes are defined as "the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes."
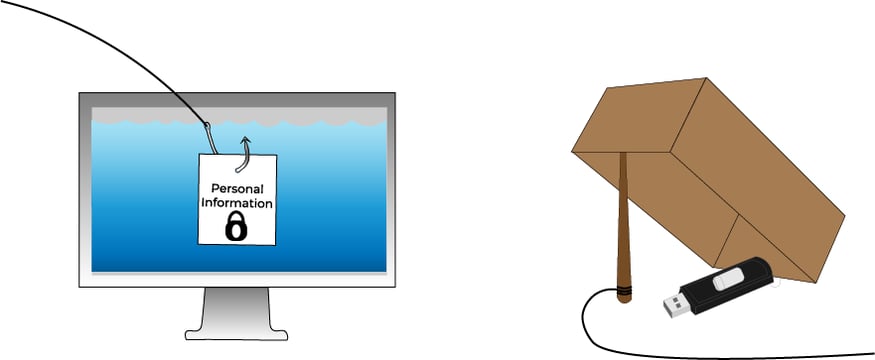
Two of the most common types of social engineering are phishing and baiting. To carry out a phishing attack on a network, a hacker mimics the emails, forms, and websites of legitimate companies in an effort to lure people into providing their company’s private information, such as credit card numbers.
Sometimes, a phishing email will contain a link to what looks like an account login page. When the victim logs into this fake page, the login information is stored and later used to hack their account.
While phishing tends to involve your email account, baiting is when a hacker places a malware-loaded item such as a flash drive in a conspicuous location and leverages human curiosity to gain access to a company’s network or victim’s computer.
For instance, a hacker with access to a company’s building could walk in and simply leave behind a flash drive loaded with malware.
When a curious employee finds it and plugs it into a computer or an Internet-connected copier, then the malware infects the network, giving the hacker access to a company’s entire network.
RELATED: 3 Social Engineering Scenarios for Your Work and Personal Life

Hackers can also access your network by testing various accounts for weak passwords. For instance, since most companies use the same format for employee email addresses, a simple search will already give a hacker half the information they need to break into an important account, like an email.
Then, the hacker can test commonly-used passwords like "abc123" or hunt online for information commonly used to create passwords, such as pets' or children's names. Employee emails are tied to so many vital company accounts. Using weak passwords gives hackers the keys to a treasure trove of company information.
If a hacker is physically close to your business' office then they can use tools like network scanners to search your network for security gaps.
Once connected to a network, a network scanner can uncover PC's or servers running outdated firmware, find operating systems with vulnerabilities such as no antivirus, and search for certain employee's computers so they know which ones to hack.
Port scanning tools can also be used to see if your network has unsecured ports, which creates security gaps.
Besides open ports, network gaps can exist in a variety of places, such as your physical hardware - for instance, your PC's -, your network infrastructure - for instance, your firewalls and switches -, your operating systems, applications, and data.
While Network-Attached Storage has its perks, like letting you have a "private cloud" in the office, when you enable file-sharing through NAS, you can potentially create gaps in your network.
If you have unsecured WiFi, such as a guest WiFi, hackers can use this security gap to breach your network.
As you can see, there are many nooks and crannies within your network that can contain security gaps, and hackers have a wide range of tools to find them. Whether you have 50 security gaps or one, keep in mind that all a hacker needs is one gap to potentially break into your network.
HR platforms. Email accounts. Sales databases. Like a web, these accounts and more are usually inter-connected because they're linked to an employee's email. If a hacker manages to break into just one of these company accounts, they could find the information to hack into them all.
Consider an employee's email as the hub of all their other accounts. This is where an employee would most likely go to reset a password for another account.
If a hacker had access to an employee's email, they could simply send password requests for other accounts to the email, and then change passwords for all those connected accounts. Hacking an employee's entire account, and then the company's network, can happen in the blink of an eye.
When hackers take your private company information, they're looking for specific information that they know will earn them a profit. Financial information such as company credit card numbers and employee social security numbers are the obvious choices, as these most directly lead to financial gain.
While exploiting confidential patient files can give a hacker access to financial information as well, the information in these files can be used to blackmail a victim with the threat of publicizing the information in the files. Files can also be held for ransom until a healthcare facility, who cannot serve patients without access to those files, pays up.
Besides these obvious choices, hackers love to sell lists of company account logins in bulk. Since sometimes these logins aren't completely accurate, they sell in bulk so that the buyer is guaranteed at least a few accounts that work.
Selling an account login for a corporate email, for instance, can let the buyer pose as you and send fake invoices to your clients.
Take this real-world example as proof of how devastating it can be when a hacker accesses an employee's email. A hacker gained access to an employee's email at a company based in Georgia and posed as them by sending invoices with just the routing number changed.
The hacker managed to steal over $500,000 before the company noticed, and by then, the money was long gone. Besides selling account logins, stealing important company documents can also be lucrativeto a hacker.
The hacker can either sell them on the dark web, publish them to harm your company's reputation, or encrypt them and hold them for ransom until you pay up.
For more information on social engineering, check out our article What is Social Engineering? [Types, Tips, and Prevention]


Once hackers take your information and publish it to the dark web, it's almost impossible to completely remove that information. Private information could be used in so many ways to harm your company's reputation and financial standing.
Hackers looking to tarnish your business' reputation can post on your social media accounts or publish damaging information. A hacker might not even need to hack your social media accounts directly to obtain the passwords to them.
In companies, sometimes, especially when multiple employees handle social media accounts, the same generic password is used across multiple accounts. This means that if a hacker figures out one easy password, they can use that password to hack other accounts that use the same password.
Stealing private information can also harm your company's bottom line, seeing as it can be used for a host of nefarious tactics. By gaining access to employee social security numbers, hackers can steal employee identities.
If hackers gain access to employee email accounts, especially those in sales or admin, they can create fake invoices that can be used to scam customers. A hacker can send an email containing an invoice posing as you to a customer, and use the same invoice template as you to make it look legitimate.
Then, all the hacker has to do to re-route the money to them is change information like the routing number, which the average customer might not think to double check. Cyber attacks can happen as seamlessly as that and can have devastating effects.
If a hacker gains access to company or employee financial information, they can max out company and employee credit cards. HR platforms contain especially sensitive financial information such as tax documents, and therefore need to be sufficiently protected.
If hackers access your customers' private information, they can harm customers through identity fraud and more, which can leave your company potentially open to data breach lawsuits.
For more information, check out our article "How Can the Dark Web Pose Security Threats to My Business?"

Picture the dark web as a game of whack-a-mole. As one website is shut down by the FBI or Europol, five more take its place. Take famous dark web marketplace the Silk Road as an example. In 2013, the popular site for selling drugs and weapons, among other illegal goods, was shut down in a sting by the FBI.
After the Silk Road's collapse, other marketplaces popped up to take its place. Since the dark web serves as both a hotbed for illegal activity and a platform for users to anonymously voice their thoughts freely, there is demand for its continued existence.
Although there is demand, dark web users will have to become increasingly hidden if they wish to avoid the same fate as the Silk Road. We predict that in the future, the dark web community will develop advanced tactics to evade detection by the authorities.
Right now, if you download a private server such as Tor, you can easily access the dark web. In the future, however, this might change. More dark website creators could start to password-protect their sites, restrict access to paying subscribers, or restrict site access to only a list of IP addresses, among other tactics.

Currently, the Internet has 3.4 billion users. Individuals and businesses alike are flocking online due to the ease with which one can run a business, shop, communicate with friends, and so on.
The downside to our increasingly Internet-savvy world is that more and more personal data is being stored online, from credit card numbers on online shopping websites to medical data on healthcare platforms.
This means that hackers, who grow more sophisticated by the day, have more access to this data. Lucrative data like social security numbers can be sold on the dark web, creating a demand on dark web marketplaces.
We predict that in the future, the dark web's most popular good for sale will increasingly become lists of personal data. Personal data such as social security numbers are sought after for the obvious financial gain, but even seemingly innocuous lists of corporate account logins and files can be used to make money through a ransomware attack.
For more information, check out our article "The Future of the Dark Web"

Even if you never go on the dark web, your personal information could still be floating around on it. As a cyber security company, we have found more times than not, new clients often have old and current passwords sitting on the dark web, waiting to be found.
Once your credentials are released on the dark web, there isn't much you can do to remove them. However, there are various preventative measures you can take to protect your devices from hackers.
While computers are designed to not make mistakes, hackers know that humans are prone to errors. That is why they exploit human error to gain access to a network and deploy ransomware. A popular way that hackers gain access to a network is through phishing attacks.
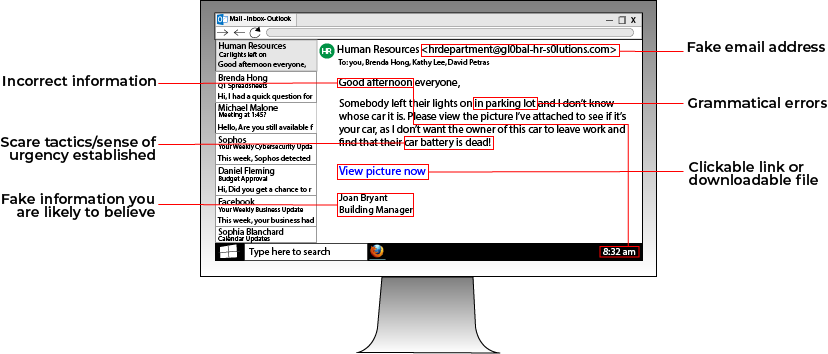
Phishing attacks involve a hacker sending an email containing a malware-loaded link to a potential victim. The email can either contain an enticing offer, such as "Click this link for a free cruise!' or can be faked to resemble a legitimate company. For instance, a hacker posing as Google could email a victim telling them to click a link to update their email storage.
Always be wary of emails from people you don't know telling you to click a link. If you want to see if an email is a phishing email, you can look at the address that the email is from. For instance, a phishing email posing as Facebook that has the email address "security@fakebookalerts.live" is probably a fake address.
Make sure that the address is spelled correctly too with no character substitutions. While an address from "@facebook.com" might be legitimate, an email from "@facebo0k.com" is probably a phishing attempt.
Another way to test a phishing email is to try and find the page the email is referencing without clicking the link.
For instance, if the email is from Microsoft and is telling you to update your storage, try doing that through the official Microsoft website instead of through the link. If you can't find such a page, then the email is most likely a phishing attempt.
In general, most legitimate emails don't ask you to click a link to validate or update information, so your internal warning signals should flash as soon as you see this. If you feel suspicious about an email, try calling the company who it's from to ask about the email, along with other verification methods.
RELATED: What is Phishing? [Types and Tips to Prevent]

Weak passwords are one of the easiest ways that a hacker can break into your network and install ransomware. Consider strengthening your passwords and protecting where they're stored to better leverage your cyber security infrastructure.
A main focus of any password policy should be to limit how much you write down your passwords, whether they're on a sticky note, an Excel spreadsheet, or in the Notes app on your phone. Writing a password down anywhere leaves it susceptible to being found by hackers.
If you write account passwords down on your phone, all it takes is your phone being stolen or your iCloud account being hacked for somebody to have the logins to accounts that contain sensitive information such as your credit card number.
If you have too many passwords to remember, consider a secure password-storing program such as LastPass.
To maintain strong passwords, consider changing passwords every six months and creating passwords that don't use easy-to-find information such as birthdays or your children's names. When creating a password, make sure it's long and complex.
Additionally, install two-factor authentication on your devices if possible, seeing as it's a widely used secure method of protecting accounts.

All the above advice will provide your company with a solid foundation to protect your network from hackers and other cyber criminals.
One of the best ways to truly and holistically secure your business' network is by hiring managed IT services to proactively monitor for and protect your network from cyber threats.
Managed IT services are just what they sound like− IT services managed by a third-party company. They monitor and protect your network from cyber threats while optimizing business processes, backing up data, and minimizing network downtime.
Having proper IT support is becoming more important each year as cyber threats are constantly on the rise. Businesses whose networks stay stagnant or aren't constantly monitored are at a high risk of being victimized by a cyber attack, experiencing severe network downtime, and more.
For those who don't wish to build an in-house IT department, managed IT services provide a strong alternative. They ensure that you have dedicated personnel to actively monitor and protect your network from the cyber threats of today and tomorrow.
IT professionals are well-versed in how to monitor and manage a company’s network and can work with you to build a comprehensive protection plan through sound maintenance and prevention practices.
Some Managed IT Service Provider use dark web scans to determine which company data has been compromised or published to the dark web. Though your credentials can be difficult to remove from the dark web, knowing which information has been published or compromised can reveal which security steps should be taken next.
At SOS, our managed IT services offering includes:
Dark web monitoring− Our dark web scans show which company data has been exposed or published to the dark web in the past 3 years, which drives immediate security decisions
Data security− BCDR plan implementation and data privacy regulatory compliance
Customer service− 24/7 assistance from a Network Operations Center with higher customer satisfaction ratings than Amazon and Ritz-Carlton
Project management− Assistance in planning office expansions, moves, remote transitions, and more
Employee cyber security education− Courses and phishing tests
If you're interested in learning more about our offering for metro-Atlanta businesses, click here. If not, then we hope that this dark web guide answered your questions.
The online world changes so frequently that your company cannot afford to get left behind. Use this guide as a resource for establishing effective network security in your company today.